Hash Encryption in Blockchain
This blog will discuss hash encryption and its working mechanism. Encryption can be defined as technical processes that secure data and systems. Encryption helps in making it harder for hackers to obtain unauthorized access to data or interfere with networks and transactions.
Encryption in modern cryptography often involves converting readable unencrypted data into an encrypted message (indecipherable encrypted data) using an encryption method or cipher. Only those with access to the data may decipher the encrypted message back into understandable plaintext. The blockchain is a fundamental mechanism that can support Bitcoin. In addition, it is a decentralized infrastructure that employs a chained data structure to validate and store information and a distributed node consensus mechanism to generate and update information. It has become a widely researched issue. This is because of its decentralization, reliability, validity, and anti-tampering qualities. For privacy protection in digital currency, focusing on encrypting data mechanisms, the significance of anonymity, and privacy-protective measures are critically necessary for blockchain technology.
The phrase “hash function” comes from the French word “hacher,” which implies “to chop into small bits,” indicating that a hash function is intended to “chop” the data.
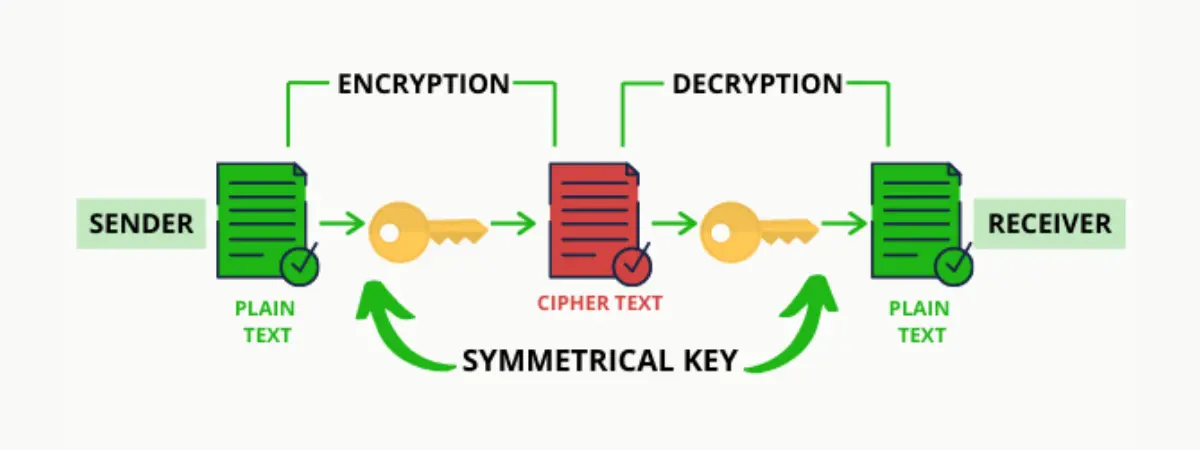
Hash functions are critical for ensuring the digital ledger’s immutability. If a blockchain’s hash algorithm is flawed, an attacker could identify collisions for essential hash values (such as the chains of a block or the importance of a Merkle tree). However, this would make it easier for malicious nodes to change the history of the blockchain network and cause a blockchain system to fail. This process of Encryption and back into decryption, from plain text to cipher-text and back to plain text, often entails the use of encryption algorithms and keys. Cryptographic techniques are mathematical procedures that can scramble plaintext (the input) into cipher text (the output) (the output).
Likewise, the key generated by the procedure turns the resulting cipher text back to its original form which is readable, and the other way around. The security of a system relies on a powerful encryption technique that can’t be readily hacked and keeps the key concealed from possible attackers.
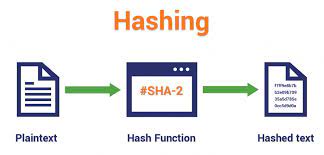
A “key” is data in string or bits – or in simple terms, a string of numbers or letters – that is fed into the encryption method. Keys are usually randomly generated and, unlike a password, are not intended to be memorized by a user to input. A hash is a mathematical expression that turns a piece of arbitrary-length information into a fixed-length encrypted output. As a result, its unique hash will always be the same size, regardless of the original quantity of data or file size involved. Hashes can’t be used to “reverse-engineer” the inputs from the hashed result, either. Some of the importance of hash encryption are:
- It is the backbone of crypto security.
- Generally employed for security purposes.
- A hash function converts a string of bytes with a specified length and structure from a random input of data (keys) (hash value).
- A transaction’s hash makes it simple to identify transactions on the blockchain.
Moreover, hash functions are commonly employed in blockchain to ensure the immutability and integrity of data stored on the distributed ledger. Because the catalog is stored decentralized, with each node keeping its own copy, ledger immutability is crucial. Otherwise, nodes may alter their ledger versions to their own advantage, disrupting the network’s agreement.
As a result, hash function security is essential to blockchain security. Using hash encryption ensures a secure blockchain community. The entire system’s security is compromised if a blockchain’s hash function becomes subject to assault.
Check this Blog out. 5 Key Skills to a Find Job in Big Data Market: https://statusneo.com/5-key-skills-to-find-job-in-big-data-market/
Add Comment
You must be logged in to post a comment.