Maximizing Cybersecurity with a Secure Software Development Life Cycle (SSDLC)
What is Secure SDLC?
Software development has become an integral part of modern business operations, with applications and systems being built to meet various organizational needs. As these systems handle sensitive information, it is essential to ensure that they are secure and free from vulnerabilities. This is where Secure Software Development Life Cycle (SDLC) comes into play.
Secure Software Development Life Cycle (Secure SDLC) is a systematic approach to integrate security into every stage of the software development process. It aims to identify, prevent, and mitigate potential security threats and vulnerabilities that can be introduced during the development of software applications and systems. The goal of Secure SDLC is to build secure systems, minimize risk, and comply with industry regulations and standards.
Secure SDLC is an essential aspect of software development that helps organizations to ensure that their applications and systems are secure and free from vulnerabilities. The process involves integrating security into every stage of the software development process, from requirements gathering to deployment. This includes identifying security requirements, incorporating security into the design and development of the application, testing for vulnerabilities and security threats, and deploying the application with appropriate security measures in place.
Secure SDLC also includes the use of secure coding practices, the implementation of encryption, the use of secure libraries and frameworks, and the conduct of security testing, such as penetration testing and code review. This helps to identify and address any security weaknesses early in the development process, reducing the risk of security incidents.
In summary, Secure SDLC is a proactive approach to security that helps organizations to build secure systems, reduce risk, and comply with industry regulations and standards. By integrating security into every stage of the software development process, organizations can ensure the security of their applications and systems, and protect sensitive information and data.
Significance of Secure Software Development Life Cycle (SDLC)
The need for a secure SDLC arises from the increasing reliance on software systems and applications in modern business operations. These systems handle sensitive information and data, making them a target for malicious actors and cyberattacks. As a result, it is essential to ensure that these systems are secure and free from vulnerabilities.
- Minimizes Risk: By integrating security into every stage of the software development process, Secure SDLC helps organizations to minimize the risk of security incidents and breaches, such as data theft, unauthorized access, and malicious attacks.
- Meets Regulatory Requirements: Compliance with industry regulations and standards, such as PCI DSS, HIPAA, and GDPR, is becoming increasingly important for organizations. A secure SDLC process helps organizations to meet these regulatory requirements and ensure the security of sensitive information and data.
- Improves Software Quality: Integrating security into the development process improves the overall quality of the software, making it more secure and reliable.
- Protects Sensitive Information: Software systems and applications handle sensitive information and data, making them a target for malicious actors and cyberattacks. Secure SDLC helps organizations protect this sensitive information and data by proactively identifying and addressing potential security threats and vulnerabilities.
- Increases User Trust: Secure SDLC helps organizations to build secure systems that users can trust, increasing user satisfaction and loyalty.
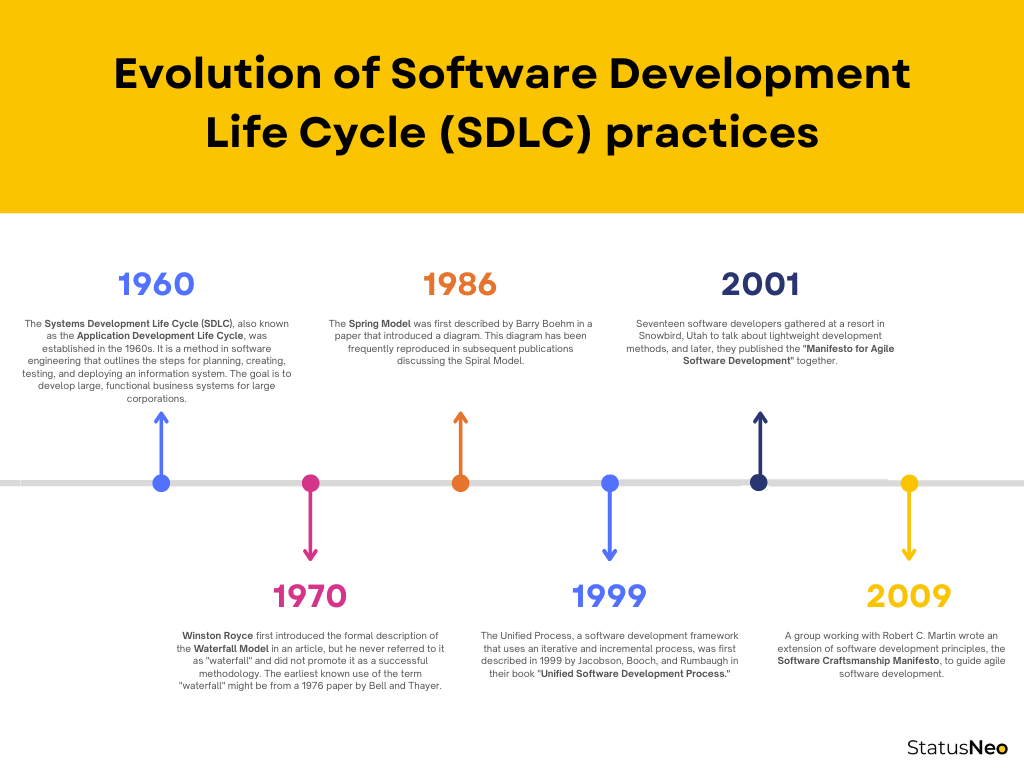
Evolution of Software Development Life Cycle (SDLC) practices
The history of Software Development Life Cycle (SDLC) practices can be traced back to the 1960s, when the concept of systems development life cycle was first introduced. At that time, software development was a manual process and the focus was on delivering functional software systems.
In the 1970s, the concept of SDLC evolved to include the Waterfall model, which was the first formalized methodology for software development. This model consisted of sequential stages, including requirements gathering, design, development, testing, and deployment. The Waterfall model was widely adopted and remains one of the most widely used SDLC models today.
In the 1990s to early 2000s, the Agile methodology was introduced, which emphasized iterative development and close collaboration between developers and customers. This methodology became popular in the software industry and remains one of the most widely used SDLC methodologies today.
In recent years, the focus of SDLC practices has shifted towards security, with the introduction of the concept of Secure SDLC. This has been driven by the increasing reliance on software systems and applications in modern business operations, the increasing threat of cyberattacks, and the need to comply with industry regulations and standards.
SDLC and application security
The security of software applications has always been a concern, but it has become even more crucial in the interconnected world of today. Back in 1970, most attacks required physical access to the machine running the application and the lack of interconnectedness reduced the risk of external actors impacting security. However, as new software development methodologies were adopted, security was not given adequate attention within the SDLC.
As a result, application security became the responsibility of IT security teams dedicated to application support. At first, security testing was done only after an application’s release, in production environments, and usually once a year. This left potential vulnerabilities open to exploitation for weeks or months before they could be detected and fixed. To mitigate this, companies started supplementing production testing with pre-release security testing, which became a critical step in the release process and applications had to pass the security check before deployment.
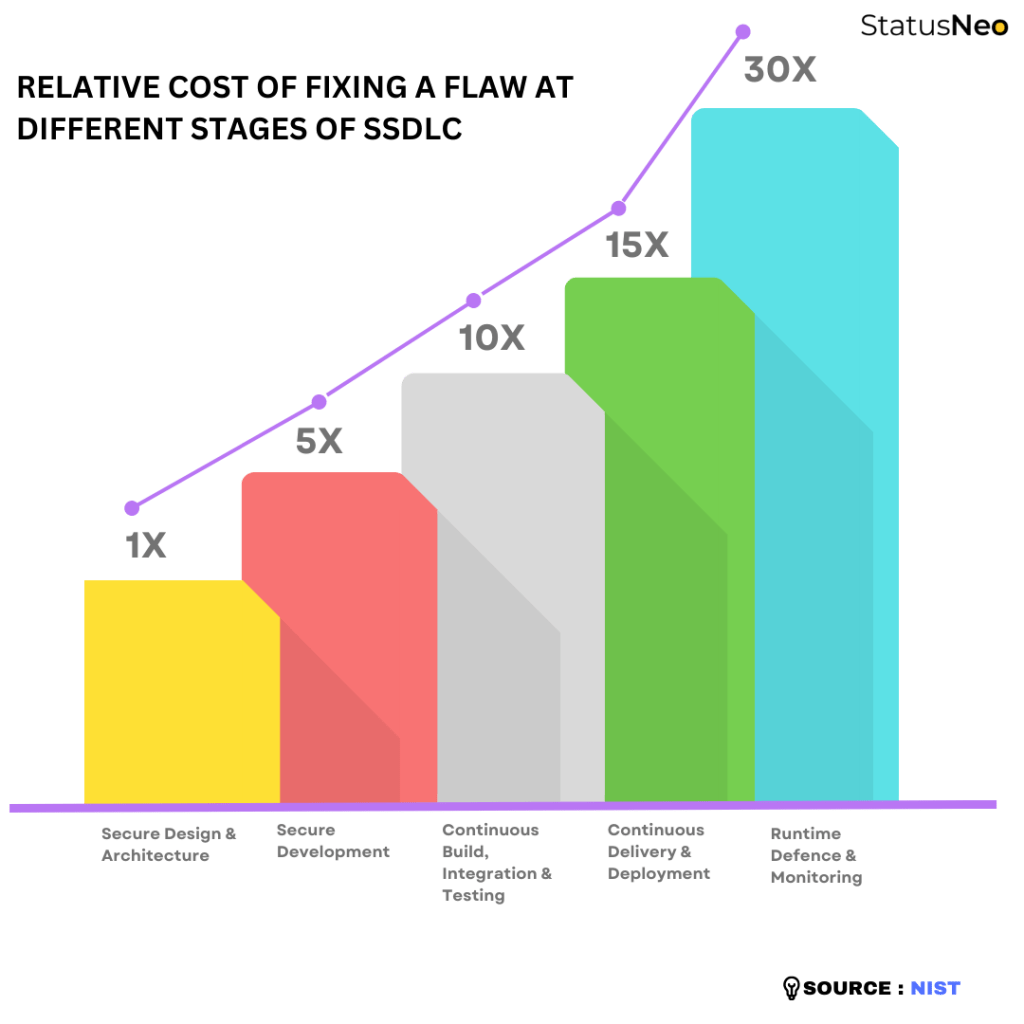
The security testing step often takes several weeks to complete, extending the release cycle. The outcome is unpredictable; a security test may find a few vulnerabilities that can be fixed quickly or dozens or even hundreds of vulnerabilities that require significant code changes and retesting. This can result in developers facing weeks of delays and missing release deadlines, causing friction within organizations and forcing companies to choose between releasing applications with vulnerabilities or missing delivery targets, or both. Additionally, fixing an issue discovered this late in the SDLC can cost up to 30 times more than fixing it early in the process.
As the speed of innovation and frequency of software releases have increased, these problems have become even more pronounced, leading to the reimagining of the role of application security in the SDLC and the creation of a secure SDLC.
Secure SDLC processes
Incorporating security into the SDLC requires a proactive approach in every stage of the software development process. This means identifying and addressing security concerns during the requirements and development phases, instead of waiting until they become issues in the deployed application. A secure SDLC integrates security considerations into every stage of the software development process.
Having a secure mindset is important, but security tasks and considerations in each SDLC phase will differ.
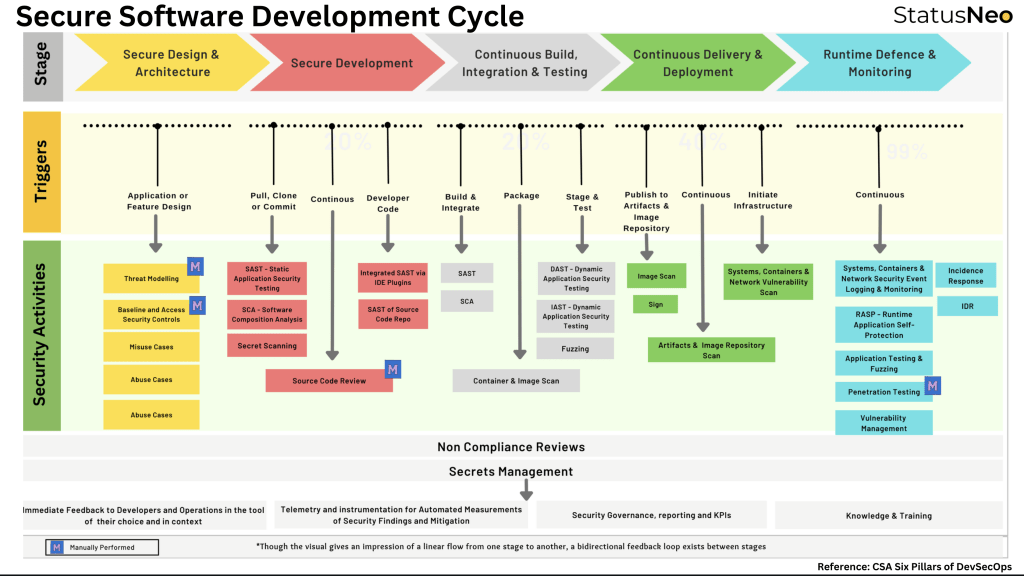
5 phases of Secure SDLC
The 5 phases of Secure SDLC with additional details and sample tasks and activities involved are:
1. Secure Design & Architecture
The Secure Design & Architecture stage of the Secure Software Development Life Cycle (SSDLC) is a crucial stage in the development process where security is integrated into the design of the software system. This stage involves identifying and addressing potential security risks, threats, and vulnerabilities in the software system before it is built. The goal of this stage is to build a secure foundation for the software and to make it more resilient to attacks.
Here are some of the activities performed in the Secure Design & Architecture stage and the tools/methods that can be used for each activity:
- Threat Modelling
Threat modeling is a process of identifying, analyzing, and prioritizing potential threats and vulnerabilities in the system. It helps to understand the potential impact of a security breach and to identify the security controls that are necessary to mitigate those risks.- Tools: Microsoft Threat Modeling Tool, IriusRisk, ThreatModeler.
- Methods: STRIDE, PASTA.
- Baseline and Access Security Controls
Baseline and access security controls are the minimum set of security controls that must be in place to protect the system and its assets. The goal of this activity is to ensure that only authorized users have access to the system and its assets and that all security-related events are recorded and monitored.- Methods: Access Control Lists (ACLs), Role-Based Access Control (RBAC).
- Methods: Access Control Lists (ACLs), Role-Based Access Control (RBAC).
- Misuse Cases
Misuse cases are a representation of how an attacker might misuse the system and its components. The goal of this activity is to identify potential attack scenarios and assess the potential impact of each scenario. This information can then be used to identify and prioritize the security controls that are necessary to prevent or mitigate these scenarios.- Tools: Use Case Modeling tools, such as IBM Rational DOORS.
- Methods: Threat Assessment, Attack Tree Analysis.
- Abuse Cases
Abuse cases are similar to misuse cases, but they focus on potential abuse scenarios, such as the abuse of system privileges or the exploitation of system weaknesses. The goal of this activity is to identify potential abuse scenarios and assess the potential impact of each scenario. This information can then be used to identify and prioritize the security controls that are necessary to prevent or mitigate these scenarios.- Tools: Use Case Modeling tools, such as IBM Rational DOORS.
- Methods: Threat Assessment, Attack Tree Analysis.
- Secure Design Patterns
Secure design patterns are proven and tested design patterns that can be used to improve the security of the software system. These patterns address common security concerns, such as input validation and defense in depth, and can be used to ensure that the software design is secure and resilient to attack.- Tools: OWASP Cheat Sheets, Microsoft’s Security Development Lifecycle.
- Methods: Least Privilege, Defense in Depth, Input Validation.
2. Secure Coding
The Secure Coding stage of the Secure Software Development Life Cycle (SSDLC) focuses on writing secure code to prevent vulnerabilities and ensure the security of the software. This stage is important because it helps catch and fix security issues early in the development process before they can become larger problems.
Here are some of the activities performed in the Secure Coding stage and the tools/methods that can be used for each activity:
- SAST (Static Application Security Testing)
This activity involves the use of automated tools to scan the source code for vulnerabilities and security issues without actually executing the code. This enables developers to identify and fix security issues early in the development process, reducing the risk of exploitation.- Tools: Veracode, Checkmarx, SonarQube, HP Fortify, etc.
- Methods: Taint Analysis, Control Flow Analysis, Data Flow Analysis, etc.
- SCA (Software Composition Analysis)
This activity involves the analysis of third-party components used in the software to identify any known vulnerabilities or security issues. This helps to ensure that the software being developed does not contain any known security risks from these components.- Tools: Nexus IQ, Black Duck, WhiteSource, etc.
- Methods: Package Analysis, Library Identification, Dependency Analysis, etc.
- Secret Scanning
This activity involves the scanning of source code for secrets such as API keys, passwords, and other confidential information that could be exploited if compromised. This helps to identify and mitigate risks associated with the accidental exposure of sensitive information.- Tools: GitHub Token Scanning, Gitrob, Trufflehog, Gitleaks, etc.
- Methods: Pre-Commit Secret Scanning, Post-commit Secret Scanning, Pattern Matching, Regular Expression Analysis, etc.
- Integrated SAST via IDE Plugins
This activity involves integrating SAST tools directly into the development environment to allow for real-time security analysis of the code as it is being written. This helps developers to address security issues more quickly and efficiently.- Tools: Sonarlint, Veracode IDE Plugins, Checkmarx IDE Plugins, etc.
- Tools: Sonarlint, Veracode IDE Plugins, Checkmarx IDE Plugins, etc.
- SAST of Source Code Repo
This activity involves scanning the source code repository to identify any vulnerabilities or security issues in the code. This helps to ensure that the entire code base is secure and free of security risks.- Tools: GitHub Actions, Jenkins, etc.
- Methods: Automated Scanning of Source Code, Continuous Integration/Continuous Deployment (CI/CD) Workflow Integration, etc.
- Source Code Review
This activity involves a manual review of the source code by security experts to identify any security risks and vulnerabilities that may not have been detected by automated tools. This helps to ensure that the code is secure and meets the required security standards.- Tools: PullRequest, CodeClimate, etc.
- Methods: Peer Review, Code Walkthrough, Code Inspection, etc.
These activities are critical in ensuring that the software design and architecture are secure and free of vulnerabilities, thereby reducing the risk of exploitation by malicious actors.
3. Continuous Build, Integration & Testing
The Continuous Build, Integration & Testing stage of the Secure Software Development Life Cycle (SSDLC) is the stage where the code changes are built and integrated continuously to verify their compatibility with the rest of the codebase and to detect any security vulnerabilities.
Here are some of the activities performed in the Continuous Build, Integration & Testing stage and the tools/methods that can be used for each activity,
- SAST (Static Application Security Testing)
SAST tools are usually integrated into the Continuous Integration (CI) pipeline to automatically scan the code for security vulnerabilities as soon as new code is committed. It involves testing the source code of the application for vulnerabilities, such as buffer overflows, SQL injections, etc. before the application is deployed. SAST can be integrated into the build process to ensure that code changes are tested before they are deployed to production.- Tools: Veracode, SonarQube, Checkmarx, Fortify, Protecode
- Methods: Code analysis, vulnerability scanning, and reporting of potential security issues in the code.
- SCA (Software Composition Analysis)
SCA tools are usually integrated into the CI pipeline to detect and alert on any known security vulnerabilities in open source components used in the codebase. It involves identifying the third-party components used in the application and checking if they have any known vulnerabilities. It helps in managing the security risks posed by these components.- Tools: WhiteSource, Nexus IQ, Snyk, GitHub Advanced Security
- Methods: Identification and management of open-source components and dependencies used in the application to minimize risks and vulnerabilities.
- DAST (Dynamic Application Security Testing)
DAST tools are usually integrated into the Continuous Deployment (CD) pipeline to automatically test the application for security vulnerabilities while it is running. It involves testing the application for vulnerabilities during runtime by sending different types of inputs and observing the application’s behaviour. DAST can be integrated into the build process to provide continuous security testing throughout the development cycle.- Tools: OWASP ZAP, WebInspect, Burp Suite, Nessus
- Methods: Testing the application from an attacker’s perspective by attempting to identify security vulnerabilities through automated and manual testing techniques.
- IAST (Interactive Application Security Testing)
IAST tools are integrated into the application runtime to monitor and identify security vulnerabilities in real-time. It combines both SAST and DAST and provides real-time feedback on security vulnerabilities during runtime.- Tools: Veracode IAST, AppScan Source, Contrast Security
- Methods: Combining dynamic testing techniques with code analysis to monitor application behavior in real-time and identify security risks.
- Fuzzing
It involves sending random and unexpected inputs to the application to identify if the application can handle such inputs and if not, how it reacts. Fuzzing can be used to identify security vulnerabilities such as buffer overflows, cross-site scripting, etc.- Tools: AFL, Peach, Sulley, JFuzz
- Methods: Automated testing technique that involves sending random, invalid, or unexpected input to the application to identify potential vulnerabilities.
- Container & Image Scan
It involves scanning the containers and images used in the application to ensure that they are free of vulnerabilities and comply with security policies.- Tools: Aqua Security, Sysdig, Tripwire, Anchore
- Methods: Scanning of containers and Docker images to identify vulnerabilities, misconfigurations, and other security risks
These tools are integrated into the Continuous Build, Integration & Testing stage to automate the testing process and ensure that security issues are detected and addressed before the application is deployed.
4. Continuous Delivery & Deployment
The Continuous Delivery & Deployment stage of the Secure Software Development Life Cycle (SSDLC) focuses on ensuring the security of the application artifacts and infrastructure that are used to deploy the software.
Here are some of the activities performed in the Continuous Delivery & Deployment stage and the tools/methods that can be used for each activity
- Image Scan
This activity involves scanning the images used for deployment, such as Docker images, for vulnerabilities and misconfigurations.- Tools: Aqua Security, Snyk, Black Duck, Trivy, Clair
- Method: Using a Continuous Integration/Continuous Deployment (CI/CD) pipeline to automate the image scanning process.
- Sign
This activity involves adding a digital signature to the application artifacts to ensure their authenticity and integrity.- Tools: GnuPG, Keybase, OpenSSL
- Method: Digital signature of the artifacts/images to ensure authenticity and integrity.
- Systems, Containers & Network Vulnerability Scan
This activity involves scanning the infrastructure used for deployment, such as servers, containers, and networks, for vulnerabilities.- Tools: Nessus, OpenVAS, Tenable.io, Qualys, AWS Inspector, Azure Security Centre
- Method: Integrating vulnerability scanning tools in the CI/CD pipeline to identify and fix vulnerabilities before deployment.
- Artifacts & Image Repository Scan
This activity involves scanning the repository where the application artifacts and images are stored for vulnerabilities and misconfigurations.- Tools: Nexus IQ, Black Duck, Snyk
- Method: Scanning the artifacts and images stored in the repository for vulnerabilities and policy violations before deployment.
5. Runtime Defense & Monitoring
The Runtime Defense & Monitoring stage is a critical component of the Secure Software Development Life Cycle (SSDLC) that helps organizations protect their applications and systems from potential security threats and vulnerabilities in real-time. The objective of this stage is to continuously monitor, detect, and respond to security incidents as they occur, thus reducing the impact and likelihood of successful attacks.
Here are some of the activities performed in the Runtime Defense & Monitoring stage and the tools/methods that can be used for each activity.
- Systems, Containers & Network Security Event Logging & Monitoring:
This activity involves continuous monitoring of security logs and events to identify potential security incidents and vulnerabilities. This helps to detect and respond to any security breaches in real-time.- Tools: ELK Stack, Graylog, Splunk, Nagios.
- Methods: Event Correlation, Anomaly Detection.
- RASP – Runtime Application Self-Protection
RASP is a technology that provides real-time protection against threats and attacks. It operates within the application runtime environment and provides continuous monitoring and protection of the application.- Tools: Signal Sciences, Runtime Shielding, Waratek.
- Methods: Application Firewalling, Input Validation, Output Encoding.
- Application Testing & Fuzzing
This activity involves testing the software for vulnerabilities and weaknesses by using techniques like fuzz testing to find unexpected input combinations that can cause crashes or unexpected behavior.- Tools: AFL, OSS-Fuzz, Codefuzzer.
- Methods: Black Box Testing, Gray Box Testing, White Box Testing.
- Penetration Testing
Penetration testing is a simulated attack on the software to identify vulnerabilities and weaknesses. This helps to identify and address any security vulnerabilities that might not be detected during other testing activities.- Tools: Metasploit, Nessus, OWASP ZAP.
- Methods: Ethical Hacking, Social Engineering.
- Vulnerability Management
Vulnerability management is the process of identifying, assessing, and prioritizing vulnerabilities in the software. This includes regularly monitoring and updating software to address any new vulnerabilities that are discovered.- Tools: Tenable, Qualys, OpenVAS.
- Methods: Vulnerability Scanning, Vulnerability Assessments.
- Incident Response
Incident response is the process of preparing for, detecting, and responding to security incidents. This includes having an established plan in place for responding to incidents, as well as having the necessary resources and capabilities to quickly and effectively respond to incidents.- Tools: Carbon Black, Tanium, McAfee.
- Methods: Threat Intelligence, Containment, Remediation.
- IDR
IDR stands for “Intrusion Detection and Response”. This activity involves monitoring the software and network for signs of intrusion, and responding to incidents by taking appropriate actions to contain and remediate the intrusion. This helps to prevent or minimize the impact of security incidents.- Tools: Snort, Suricata, Bro.
- Methods: Signature-Based Detection, Anomaly-Based Detection.
Benefits of SSDLC
Secure SDLC is an example of a “shift-left” approach, where security checks are integrated as early as possible in the software development life cycle. This helps development teams plan releases better, making it easier to identify and resolve any issues that could impact the release timeline. Early detection is preferred to fixing security problems after the application has been deployed to production. SSDLC also enables the development team to lead the security efforts, giving them ownership of the quality of their applications and resulting in more secure deployments.
Most of the security testing within the SDLC process can now be automated, especially in the DevOps environment, which requires close collaboration between DevOps and the engineers implementing the application’s functionality. This collaboration needs to be integrated into the SDLC itself. By addressing security issues early on, development teams can minimize the overall cost of ownership of their applications. Late discovery of security issues can lead to a 30-fold increase in the cost of fixing them.
- Improved security: Early detection and resolution of security threats through integration of security checks throughout the SDLC.
- Enhanced release planning: Helps avoid surprises and keeps releases on track by catching and addressing issues as they arise.
- Empowerment of development team: Leads to more secure applications as the development team takes ownership of the overall quality of the applications.
- Automation: Majority of security testing can be automated, reducing manual effort and cost.
- Collaboration: Frequent collaboration between DevOps and development teams promotes continuous improvement of the SSDLC process.
- Reduced total cost of ownership: Early detection and resolution of issues reduces the cost of fixing them later in the SDLC.
Future of Security in SDLC
To ensure secure applications, traditional practices of finding vulnerabilities only during production are no longer enough. The software industry and types of attacks have evolved, making it crucial to secure every step of the software development process. This includes considering security behaviors during requirement gathering, fostering a security-focused team culture, incorporating automated verification into the deployment process, and other security-oriented practices to create a secure software development life cycle.
Shifting security risks to the left by addressing security issues during the requirements phase instead of fixing them later in the maintenance phase, leads to more secure applications. Focusing on security at every stage of development gives you the peace of mind that your application is secure.
The future of security in the software development life cycle (SDLC) will see a continued emphasis on integrating security into every stage of the process. This means that security will be viewed not as an afterthought or add-on, but as a core part of the development process. This shift towards a secure SDLC will continue to drive the adoption of automated security testing, continuous integration and delivery (CI/CD), and DevSecOps practices. Additionally, there will be a growing emphasis on collaboration between development and security teams, as well as an increased focus on education and awareness around secure coding practices. Ultimately, the future of security in the SDLC will be characterized by a proactive approach to mitigating risks and ensuring the secure delivery of high-quality software.

Add Comment
You must be logged in to post a comment.