AI in Cybersecurity: A Comprehensive Analysis of the Role of AI
In the contemporary landscape of cybersecurity, innovative and adaptive solutions are demanded due to the increasing sophistication of cyber threats. Artificial Intelligence, particularly in the form of machine learning algorithms, has emerged as a pivotal player in enhancing cybersecurity measures. This blog explores the multifaceted role of AI in proactively identifying and mitigating cyber threats, emphasizing the significance of anomaly detection and predictive analytics.
Overview of AI in Cybersecurity
AI is a game-changer in modern cybersecurity. It’s completely changing how organizations deal with constantly changing cyber threats. When we bring AI into the picture, it’s like a whole new level of power. It helps us find and respond to threats way better than before. AI uses fancy math stuff called machine learning to let computers look at a ton of data, figure out what’s normal, and spot anything that looks weird or dangerous. It can find everything from regular computer viruses to tricky, targeted attacks.
The best part is that AI doesn’t just find the threats, it helps us fight back in real time. It’s like having a super-fast and smart security guard who can adapt to whatever the bad guys throw at us. In the world of cybersecurity, AI is like a superhero. It makes our defenses stronger and helps us stay safe from all kinds of cyber risks.
Incorporating Artificial Intelligence (AI) into cybersecurity strategies goes beyond traditional defense methods. AI adds a proactive and adaptable aspect to cybersecurity. It does this by using machine learning algorithms to analyze vast datasets and detect potential threats. This includes advanced threat detection, predictive analytics, and automated responses. Importantly, AI boosts human abilities by processing and understanding data quickly and on a large scale, improving the overall efficiency of cybersecurity operations.
AI has a transformative impact on cyber resilience. It offers dynamic defense against ever-changing threats, helping organizations stay ahead of sophisticated attackers. AI-driven cybersecurity adjusts to new threats, establishing strong defense mechanisms crucial for protecting sensitive data and digital systems.
Integrating AI into cybersecurity not only expands capabilities but also plays a vital role in strengthening organizations against today’s complex threat landscape.
Let’s Explore Some Cyber Threats:
In the world of cybersecurity today, organizations face complex challenges in the digital realm. Cyber threats have become highly sophisticated, creating a dynamic and intricate environment. One significant challenge is the rise of advanced persistent threats (APTs). These threats are particularly formidable because they operate stealthily, often evading traditional security measures. APTs can remain undetected for extended periods, allowing malicious actors to infiltrate networks, gather sensitive information, and execute targeted attacks.

Adding to the complexity is the ever-evolving landscape of attack vectors. Attack vectors are the pathways through which cyber threats gain unauthorized access to systems or networks. In today’s cybersecurity landscape, these attack vectors are not static; they continually evolve to exploit new vulnerabilities and bypass existing defenses. This dynamic nature poses a significant challenge for organizations, requiring them to continually adapt their cybersecurity strategies to effectively counter emerging threats.
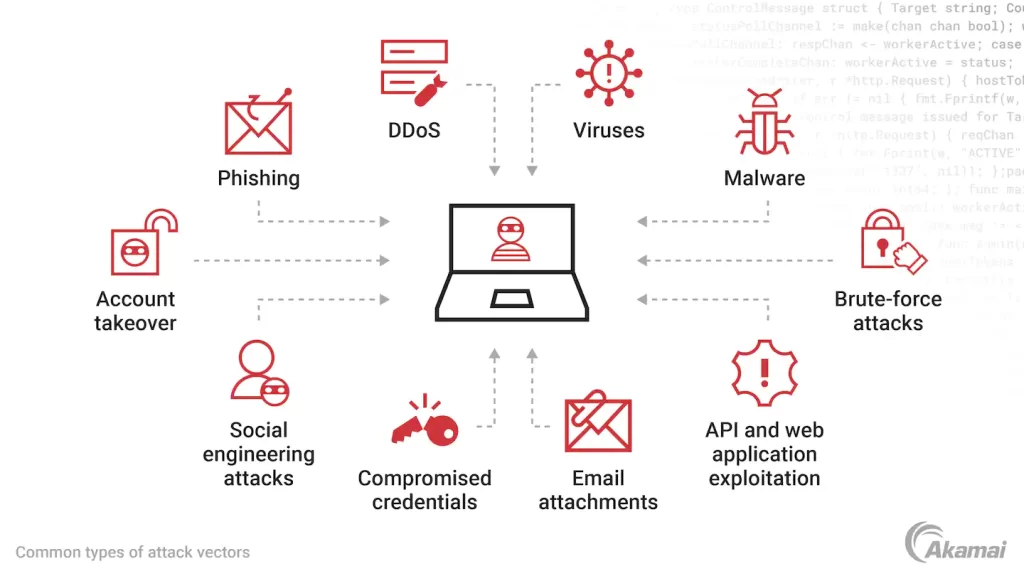
This underscores the need for a proactive and adaptive cybersecurity approach to stay ahead of the evolving threat landscape and ensure robust defense mechanisms against these advanced and dynamic cyber threats.
Let’s see some more
Cyber Threat Landscape Complexity
Today’s cyber threat landscape is intricate, with threat actors employing sophisticated techniques like APTs, polymorphic malware, and zero-day vulnerabilities. Artificial Intelligence (AI) effectively navigates this complexity due to its adaptability and learning capabilities. For instance, AI plays a crucial role in detecting APTs by utilizing machine learning algorithms that learn from historical attack patterns to identify subtle and complex threats.
Dynamic Nature of Cyber Attacks
Cyber threats are continuously evolving, demanding adaptive and real-time defense mechanisms. Machine learning algorithms, a key component of AI, dynamically analyze patterns and behaviors, enabling the detection of novel threats. For instance, AI excels at identifying new variants of malware by recognizing unusual patterns in code execution. This capability enhances our defense against dynamic and ever-changing cyber-attacks.
Data Overload and Analysis Challenges
The sheer volume of data in digital environments presents challenges for traditional cybersecurity methods. AI stands out in processing large datasets, facilitating efficient analysis of network traffic and user behavior. For instance, AI can swiftly analyze log data using machine learning algorithms, promptly identifying anomalies that may indicate potential threats within extensive datasets.
Automation and Response Time
Cyber threats unfold rapidly, necessitating automated responses. AI assists in quickly spotting and mitigating threats, reducing the time from detection to resolution. For example, AI can automate responses when an issue is detected, such as isolating compromised computers or halting malicious actions, thereby minimizing the impact of attacks.
Enhanced Threat Intelligence
AI-driven systems actively analyze vast amounts of threat intelligence data, providing actionable insights. This enriched threat intelligence empowers the implementation of proactive defense strategies. For instance, AI can analyze global threat feeds, correlating data to identify emerging attack patterns. This capability enables security professionals to prepare and strengthen defenses against evolving threats.
Let’s Talk About The Importance of AI
Proactive Threat Detection
Instead of relying on fixed rules, AI takes a proactive approach by learning from past data to detect threats before they occur. For example, AI-powered antivirus systems can identify new types of malware by recognizing patterns from previous ones, even if there are no specific rules for the new threat.
Behavioral Analysis and Anomaly Detection
AI is excellent at analyzing behavior to spot anomalies. Behavioral analytics, driven by AI, can detect deviations from normal patterns. For instance, AI can analyze user behavior and alert us to unusual activities, such as an employee accessing sensitive data outside regular working hours.
Prediction of Emerging Threats
AI’s predictive analytics helps us anticipate future threats before they become major issues. AI looks at historical data to identify patterns that might indicate upcoming problems. For example, predictive analytics can identify trends in phishing attacks, allowing us to strengthen our defenses before a significant number of attacks occur.
Adaptive and Learning Systems
AI systems continuously learn and adapt, improving their effectiveness over time. Adaptive AI algorithms enhance their understanding of new attack methods. For instance, AI used in intrusion detection systems evolves its detection capabilities based on the changing tactics used by attackers.
Efficient Incident Response
AI streamlines incident response, automating tasks when a security issue arises. This reduces the workload on human analysts. For example, AI can use predefined plans to automate our response to security problems, such as cyberattacks.
Scalability and Resource Efficiency
AI-powered cybersecurity offers scalability for managing diverse datasets. For instance, AI optimizes resource allocation by focusing on relevant threats. This ensures efficient use of computing resources, especially in environments with fluctuating data loads.
Continuous Monitoring and Adaptation
AI enables continuous monitoring, allowing us to be vigilant against cyber threats at all times. AI can adjust security rules as it receives new threat information, strengthening our defenses and enabling swift responses. This proactive approach helps us stay ahead of cyberattacks and maintain the security of our systems.
Evolution of AI Applications in The Cybersecurity Domain
The historical context and evolution of AI applications in the cybersecurity domain significantly transformed how organizations defend against cyber threats. In the early stages, cybersecurity mainly relied on static rules and predefined patterns to identify and mitigate threats. However, with the increasing complexity and sophistication of cyber threats, there was a growing need for more adaptive and intelligent defense mechanisms. This need emphasizes the crucial role played by the evolution of AI applications in cybersecurity.
Over time, AI technologies, especially machine learning algorithms, emerged as game-changers in the cybersecurity landscape. In contrast to traditional approaches, AI brings a dynamic and learning-oriented perspective to threat detection and response. The historical journey illustrates a shift from reactive cybersecurity measures to more proactive and predictive approaches. AI’s capacity to learn from historical data, identify anomalies, and predict potential threats before they fully materialize has become a cornerstone in modern cybersecurity.
- In the early stages of artificial intelligence (AI) development, which began in the 1950s, the focus was on creating rule-based systems for solving basic problems. In the cybersecurity field, this era saw the development of simple rule-based filters designed to detect known threats.
- The 1980s marked the emergence of the first-generation antivirus software as computer viruses became more common. These antivirus programs used signature-based detection, comparing known virus patterns with files on a computer. While effective against known threats, they struggled to detect more complex and new types of attacks.
- In the 1990s and early 2000s, machine learning (ML) techniques gained prominence in cybersecurity. ML introduced a new approach by allowing systems to learn from data. Anomaly detection models based on statistical methods were introduced to identify unusual behavior patterns.
- Machine learning was applied to Intrusion Detection Systems (IDS) to spot abnormal network traffic patterns. Systems moved away from relying solely on known signatures and started using behavior-based detection, which triggered alerts when deviations from normal behavior were detected.
- The 2010s witnessed the resurgence of neural networks, especially with the rise of deep learning. These neural networks proved highly effective in tasks like image and speech recognition, leading to their application in cybersecurity. Deep learning models became adept at identifying complex patterns in malware and network traffic.
- Deep learning algorithms played a vital role in endpoint protection solutions during this period. These solutions utilized neural networks to analyze how files behaved, enabling the detection of previously unseen malware and advanced persistent threats (APTs).
- Natural Language Processing (NLP) entered the cybersecurity domain, particularly for analyzing large volumes of textual threat intelligence data. NLP models were capable of extracting valuable insights from unstructured data sources, significantly enhancing the capabilities of security analysts.
Machine Learning & its Supervised & Un-Supervised Algorithms
In the realm of AI in cybersecurity, let’s closely examine machine learning algorithms, the driving force behind AI’s ability to safeguard digital spaces. Machine learning, a subset of AI, functions as the brains of the operation, equipping cybersecurity with advanced tools to comprehend and respond to intricate patterns within extensive datasets. These algorithms undergo rigorous training, learning from historical data, enabling them to identify irregularities, deviations, and potential threats. What’s remarkable is their continuous evolution, adapting to new threats, and bolstering our digital defenses.
Consider machine learning algorithms as digital sentinels, each serving as a digital detective. They play crucial roles in tasks like anomaly detection and predictive analytics, essential for fortifying our networks against cyber threats. By analyzing patterns of normal and abnormal behavior, they empower us to proactively identify potential risks before they escalate. AI’s role in cybersecurity, particularly through machine learning, revolves around intelligence and adaptability. It’s akin to having a vigilant guardian who perpetually learns and evolves to outmaneuver cyber threats. This deep dive into machine learning unveils its transformative role, shaping the future of cybersecurity.

Now, let’s unravel the concepts of supervised and unsupervised learning, two fundamental pillars of machine learning, each with distinct characteristics and applications.
Supervised learning resembles a teacher guiding a student. In this approach, we train a machine-learning model using labeled data. The labeled dataset pairs each input data point with an output label. The model’s objective is to learn the underlying patterns and relationships between inputs and outputs. Once trained, the model can make precise predictions or classifications when presented with new, unseen data. It’s akin to mirroring the guidance of a teacher. Supervised learning proves invaluable when clear distinctions exist between input and output, such as in image classification, spam email detection, or speech recognition.
On the other hand, unsupervised learning is somewhat like exploring a new city without a map or guide. In this method, explicit labels are absent. Instead, the aim is to unearth patterns and structures within the data itself. Unsupervised algorithms work diligently to reveal concealed patterns, group similar data points, or simplify complex data. It’s all about delving into data without predefined categories or labels. Unsupervised learning, however, excels when we seek to group similar customer behaviors in market segmentation, reduce data noise, or identify topics within a vast collection of documents.
Supervised learning utilizes labeled data to educate models for making predictions or classifications, while unsupervised learning ventures into unlabeled data to uncover patterns and structures. These two approaches form the bedrock of machine learning, each serving distinct roles in solving real-world challenges.
Deep Learning and NLP in Cybersecurity
Let’s explore the exciting world of cybersecurity and how we’re using deep neural networks, a pinnacle of artificial intelligence, to detect threats. Deep learning, a subset of machine learning, uses neural networks inspired by the human brain to process information in complex layers. In cybersecurity, these networks act like highly skilled guards, deciphering intricate patterns and anomalies within massive datasets. Unlike traditional methods, deep learning learns and improves its understanding of threats on its own, creating a sophisticated defense against an ever-changing landscape of cyber risks.
Applying deep neural networks in threat detection is similar to training an exceptionally perceptive guard. These networks sift through vast amounts of data, spotting subtle deviations and identifying potential threats that might escape traditional detection methods. Through continuous learning and adaptation, deep learning algorithms become skilled at recognizing even the most sophisticated and previously unseen cyber threats. Integrating deep learning into cybersecurity represents a significant shift—a move from rule-based systems to autonomous, intelligent threat detection. It’s like having a guard with an innate understanding of the digital world, capable of distinguishing friends from foes in the intricate dance with cyber adversaries. This exploration of deep neural networks showcases their transformative role in reshaping the future of cybersecurity, ushering in an era of adaptive and intelligent defense mechanisms.
Deep learning plays a pivotal role in addressing complex and evolving cyber threats by offering advanced capabilities in threat detection, classification, and mitigation. In the realm of cybersecurity, deep learning models, such as deep neural networks, excel at processing vast amounts of data and extracting intricate patterns, allowing them to adapt effectively to the dynamic nature of cyber threats. One of the key strengths of deep learning is its ability to analyze a multitude of data sources, including network traffic, system logs, and user behavior, to detect anomalies and potential threats. Unlike traditional rule-based systems, deep learning models can automatically learn and update their understanding of normal and abnormal behavior, making them well-suited for handling previously unseen and sophisticated threats.
Deep learning also excels in feature extraction, where it can automatically identify relevant features from raw data, such as identifying malicious code patterns or recognizing unusual network traffic patterns. This capability enables early threat detection and reduces false positives, which are crucial in cybersecurity to prevent both false alarms and actual threats from going unnoticed. Furthermore, deep learning can enhance the accuracy of threat classification. It can categorize different types of cyberattacks, such as malware, phishing attempts, or zero-day exploits, by learning from historical data and adapting to new attack techniques. This adaptability is vital because cyber threats constantly evolve, making it essential to have a system that can keep pace with emerging attack vectors.
Deep learning’s ability to process large and diverse datasets, learn from them, and adapt to emerging cyber threats makes it a potent tool in modern cybersecurity. Its capacity to handle complex and dynamic threats positions it as a crucial component in safeguarding digital assets and networks in an increasingly interconnected and vulnerable world.
Now, let’s delve into the intriguing realm of threat intelligence and explore the application of Natural Language Processing (NLP). NLP, a branch of artificial intelligence, is harnessed to analyze and extract meaningful insights from the vast sea of textual threat intelligence data. In cybersecurity, where information is often buried in unstructured text, NLP acts as a sophisticated interpreter, enabling the comprehension of nuances, context, and patterns within textual data.

The use of NLP in threat intelligence is akin to deploying a linguistic maestro in the cybersecurity orchestra. It navigates through diverse sources of information, deciphering the intricacies of language to unveil hidden threats. This application goes beyond mere keyword matching; NLP algorithms comprehend the semantics and intent behind the text, unraveling the subtleties that may indicate potential risks. The integration of NLP in threat intelligence signifies a leap forward in the ability to make sense of the linguistic landscape of cyber threats. It transforms raw textual data into actionable insights, providing security professionals with a nuanced understanding of potential risks. This deep dive into the world of NLP in threat intelligence unveils its role as a linguistic detective, enhancing the capacity to decipher the language of cyber threats in the ever-evolving cybersecurity landscape.
Anomaly Detection in Cybersecurity
Let’s dive into the crucial domain of Anomaly Detection in Cybersecurity. In this chapter, we’ll unravel the complex world of anomalies, which are deviations from what’s considered normal behavior, and explore their paramount importance in strengthening digital defenses.
Anomaly detection is a fundamental concept in cybersecurity. It involves identifying patterns or behaviors that stray from the established baseline of what’s considered normal. Its significance lies in its proactive role, enabling cybersecurity systems to spot irregularities that could indicate potential threats.
Think of anomaly detection as a vigilant guardian, constantly monitoring digital landscapes for any deviations from typical patterns of activity. Its importance becomes evident in the ever-changing field of cybersecurity, where traditional rule-based approaches might struggle to identify new and unfamiliar threats. Anomaly detection acts as a preemptive shield, giving organizations the ability to detect and respond to emerging threats before they become major issues.
This section delves into the heart of anomaly detection, explaining its definition, mechanisms, and its indispensable role in preserving the integrity of digital ecosystems. This exploration serves as a guide to understanding the proactive and adaptive nature of anomaly detection, which is a crucial element in the ongoing battle against the constantly evolving landscape of cyber threats.
Types of Anomalies in Cyber Threats
In cybersecurity, anomalies are unusual or out-of-the-ordinary patterns, events, or behaviors in computer systems or networks. These anomalies can indicate potential security threats or issues. Cybersecurity experts use techniques to detect these anomalies and investigate whether they could signal malicious activity or vulnerabilities that attackers might exploit.
For example, an anomaly in network traffic could be a sudden and unexplained increase in data transfer between a user’s computer and an external server. This could be a sign of a data breach or an unauthorized access attempt. Another example might involve detecting an anomaly in a user account’s behavior, like multiple failed login attempts or unusual access to sensitive files, which could suggest a potential compromise.
To identify these anomalies, cybersecurity systems often rely on machine learning algorithms. These algorithms analyze historical data to establish a baseline of normal behavior. When they come across data that significantly deviates from this baseline, they raise an alert for further investigation. Accurate anomaly detection is vital because it can help detect emerging threats and security breaches early, allowing organizations to respond quickly and protect their systems and data.
When categorizing anomalies in cyber threats, we can classify them into several types based on how they deviate from the norm. The main categories include:
- Behavioral Anomalies: These involve deviations from expected patterns of user or system behavior. Examples include unusual user access patterns, like logging in from an unfamiliar location or time, or unexpected file access. Behavioral anomaly detection relies on understanding typical behavior and flagging actions outside these norms.
- Statistical Anomalies: These are identified through statistical analysis of data. Statistical anomalies occur when data points significantly differ from the statistical properties of the rest of the dataset. For instance, sudden and significant deviations from expected statistical distributions in network traffic can indicate a statistical anomaly.
- Semantic Anomalies: These relate to discrepancies in the meaning or context of data. Instead of patterns, they focus on the content and context of information. For example, if an email contains unusual keywords or file attachments, it may be considered a semantic anomaly. Detecting these often involves natural language processing and content analysis.
Each type of anomaly detection plays a vital role in cybersecurity. They help organizations identify various potential threats, from unauthorized access to statistical irregularities to content-based anomalies like phishing attempts or malware. Understanding these different anomaly types enables cybersecurity professionals to better protect their systems and data from a range of cyber threats.
Real-World Impact of Anomaly Detection:
Let’s dive into real-world case studies to see how anomaly detection makes a difference:
- DDoS Attack Mitigation: Imagine a sudden surge in data traffic on an organization’s network. Traditional security measures might miss this anomaly, with anomaly detection triggering an alert. Further investigation reveals a sophisticated Distributed Denial of Service (DDoS) attack. Anomaly detection quickly mitigates the threat, preventing network disruption.
- Insider Threat Prevention: In another case, an anomaly is detected in an employee’s behavior pattern. They suddenly access sensitive data outside their usual work hours. This anomaly triggers an immediate response, uncovering an insider threat attempting unauthorized data access. Anomaly detection not only prevents a potential breach but also aids in insider threat mitigation.
These case studies emphasize the practical value of anomaly detection. It can identify nuanced irregularities that might otherwise go unnoticed. In essence, anomaly detection is a proactive and essential tool, providing organizations with a crucial advantage in combating diverse and evolving cyber threats.
Significance of Anomaly Detection in Cybersecurity:
Anomaly detection is a proactive defense mechanism in cybersecurity. It actively looks for deviations or unusual behaviors before they become full-scale attacks. Its importance lies in its ability to predict and respond to potential threats before they escalate.
Think of anomaly detection as an intelligent sentinel that can detect subtle changes in patterns, which traditional security measures might miss. Its proactive approach transforms cybersecurity from being reactive to anticipatory. Identifying anomalies in real-time, enables quick responses, reducing the impact of potential attacks and ensuring digital infrastructure resilience.
In essence, anomaly detection plays a dynamic and adaptive role in addressing cyber threats. It’s not just a tool; it’s a strategic asset that provides organizations with foresight and agility to navigate the ever-changing landscape of cybersecurity challenges.
Machine Learning-Based Anomaly Detection
Machine learning-based anomaly detection is a process where models are trained to spot unusual patterns or outliers in data. Here’s how it works:
- Data Collection: First, you gather a dataset that includes both normal and anomalous data samples. The normal data represents typical behavior or patterns, while the anomalous data represents deviations from the norm, which could be potential security threats or errors.
- Feature Engineering: Next, you extract relevant characteristics or features from the data. These features represent the data’s key attributes and make it suitable for machine learning algorithms. For example, in network traffic data, features might include things like packet counts, data transfer rates, or source-destination pairs.
- Algorithm Selection: Then, you choose a machine learning algorithm suitable for your specific problem and dataset. This could be decision trees, support vector machines, deep neural networks, or others. The selected model is trained using the labeled dataset, where it learns to differentiate between normal and anomalous data points by identifying patterns, relationships, or statistical differences in the features.
- Training the Model: During training, the model aims to reduce its prediction errors. It iteratively adjusts its internal parameters to make more accurate predictions about whether a given data point is normal or anomalous. Cross-validation techniques are often used to assess the model’s performance and fine-tune its parameters.
- Real-time Anomaly Detection: After training, the model is ready for real-time anomaly detection. When presented with new, unlabeled data, it evaluates the data using the patterns and thresholds it learned during training. If the model detects a deviation from the expected patterns, it raises an alert, signaling a potential anomaly that requires further investigation by cybersecurity experts.
Machine learning-based anomaly detection is valuable in cybersecurity because it can adapt to evolving threats and detect anomalies that might be challenging for rule-based systems. It’s a powerful tool for identifying both known and unknown security issues by leveraging the ability of machine learning models to learn from data and recognize subtle deviations from the norm.
Now, let’s look at the strengths and limitations of machine learning in anomaly detection within cybersecurity:
Strengths and Limitations of Machine Learning in Anomaly Detection.
Let’s explore the strengths and limitations of using machine learning for anomaly detection in cybersecurity.
Strengths:
- Adaptability: Machine learning models can adapt to evolving threats and detect anomalies that may be challenging for rule-based systems. They continuously learn from data, making them capable of recognizing new and unknown security issues.
- Efficiency: Machine learning-based anomaly detection can process large volumes of data quickly and accurately, making it suitable for real-time detection in complex and dynamic environments.
- Pattern Recognition: These models are excellent at identifying subtle patterns and anomalies in data, even in cases where deviations from normal behavior are not obvious to human analysts.
- Reduced False Positives: By learning from historical data, machine learning models can reduce the number of false positives compared to traditional rule-based systems, which helps security teams focus on genuine threats.
Limitations:
- Data Quality: Machine learning models heavily depend on the quality and representativeness of the training data. If the training data is biased or incomplete, the model’s performance may be compromised.
- Overfitting: There’s a risk of overfitting, where a model becomes too specialized in recognizing patterns in the training data but struggles with new, unseen data. This can lead to false negatives when dealing with novel threats.
- Continuous Training: Machine learning models require ongoing training to stay effective against evolving threats. This demands significant computational resources and expertise.
- Interpretability: Some machine learning models, especially deep learning models, can be complex and challenging to interpret. Understanding why a model made a specific decision can be difficult, which may be a problem in situations where explanations are necessary for compliance or accountability.
In summary, machine learning-based anomaly detection is a powerful tool for cybersecurity, offering adaptability, efficiency, and accurate pattern recognition. However, it requires high-quality data, careful model tuning, continuous training, and addressing challenges related to overfitting and interpretability. When used effectively, it enhances an organization’s ability to detect and respond to cyber threats.
Predictive Analytics for Cyber Threat Prevention
Let’s discuss how combining historical data with machine learning can help predict and prevent cyber threats.
Predictive Analytics for Cyber Threat Prevention
In our discussion, we’re going to explore how we can use historical data and machine learning to predict and prevent cyber threats. This is like having a crystal ball for cybersecurity, allowing us to foresee and stop potential threats before they become major problems.
Understanding Historical Data
Think of historical data as a vast library filled with stories of past cyber incidents. These stories contain valuable information about how threats and attacks happened. Now, imagine machine learning algorithms as experienced detectives. They are good at finding patterns and connections in these stories.
Training Machine Learning Models
To make these detectives even better, we train them using the historical data. It’s similar to how detectives study old cases to get better at spotting suspicious activities. During this training, the algorithms learn to recognize subtle patterns that might indicate a threat.
Quality Matters
But here’s the catch: the quality and diversity of historical data matter a lot. If we have a wide range of cyber incidents over time in our data, it helps the algorithms become more accurate at predicting threats.
Real-World Success Stories
Now, let’s look at some real-world examples of how predictive analytics has helped prevent cyber threats:
- Banking Security: A major bank used predictive analytics to detect fraud. By looking at past transaction data and customer behaviors, they created a model that could spot unusual patterns linked to fraud. When this model noticed something fishy, it sent out alerts for further investigation. This helped the bank stop fraudulent transactions and protect its customers.
- Healthcare Data Protection: In the healthcare sector, a large hospital network uses predictive analytics to predict and prevent data breaches. By analyzing who accessed patient records and how they did it, they could identify unauthorized access attempts. This early warning system allowed them to prevent data breaches, ensuring patient privacy and staying compliant with regulations.
- E-commerce Security: An online retailer used predictive analytics to fight cyber threats. They looked at how users logged in and what they bought. If their model detected strange account activity, possibly indicating an account takeover, it required extra verification steps before granting access. This protected customer accounts and ensured safe shopping.
These examples show how predictive analytics can help organizations stay ahead of cyber threats. By using historical data and advanced algorithms, they can identify suspicious activities early, taking action to protect sensitive information, financial assets, and customer trust. This proactive approach strengthens cybersecurity defenses and keeps us safer in the digital world.
The Impact of Predictive Analytics on Reducing Response Time
Let’s discuss how predictive analytics can significantly reduce response time in cybersecurity.
The Impact of Predictive Analytics on Reducing Response Time
In our discussion, we’ll explore how predictive analytics makes a big difference in speeding up cybersecurity responses. It’s like having a superhero that not only sees trouble coming but also takes action before it hits.
The Traditional Way
Think about how things usually work in cybersecurity. We often react to threats after they’ve already caused damage. This reactive approach means there’s a delay between spotting a threat and doing something about it.
Predictive Analytics as a Visionary Sentinel
Now, imagine predictive analytics as a superhero with the power to predict threats. It does this by looking at historical data and using smart algorithms. Instead of waiting for something bad to happen, it can see trouble coming from a mile away.
The Big Impact
The real magic happens when predictive analytics spots potential threats before they become serious. By recognizing patterns and weird things that might mean a cyber-attack is on the way, organizations can act early. This means they can stop the threat or reduce its impact way faster than reacting later.
Imagine a Cybersecurity Crystal Ball
Think of predictive analytics as a crystal ball for cybersecurity. It not only tells us when the storm is coming but also helps us prepare. Being proactive like this means we have our defenses ready, and the window of vulnerability is much smaller.
Turning the Tables on Cyber Threats
In the end, predictive analytics turns the tables on cyber threats. It changes cybersecurity from a reactive mode to a proactive one, where we’re ready for whatever comes our way. This agility and readiness make our defense stronger and more resilient against potential risks in the ever-changing digital world.
Challenges and Ethical Considerations
Let’s talk about the challenges and ethical concerns that come with using predictive analytics in cybersecurity.
Challenges and Ethical Considerations in Predictive Analytics for Cybersecurity
Using predictive analytics in cybersecurity isn’t without its difficulties and ethical issues. Here are some of the main challenges:
1. Handling Big and Varied Data: First, there’s a ton of data in cybersecurity, and it’s not all the same. Sorting through this data, cleaning it up, and making sure it’s accurate is tough. If the data isn’t good, our predictive models won’t work well.
2. Ever-Changing Threats: Cyber threats are always changing. Bad actors come up with new tricks all the time. This means that predictive models, which are based on past data, might not catch these new threats. So, we have to keep our models up-to-date.
3. Figuring Out What’s Real: Predictive analytics can sometimes get things wrong. It might raise an alarm when there’s no real threat (a false positive) or miss a threat that’s there (a false negative). We have to find the right balance to avoid either alerting too often or missing real dangers.
Now, for the ethical stuff:
4. Privacy Concerns: Predictive models need a lot of data, and that might include personal information. We have to be careful not to invade people’s privacy when using this data. It’s crucial to be transparent about what data we use and why.
5. Bias and Fairness: These models learn from old data, and if that data had biases in it, the models might repeat those biases. This could lead to unfair treatment of certain groups or individuals. We need to be aware of this and make sure our models are fair.
6. Transparency and Accountability: People should know how these predictive models work, what data they use, and what they might predict. Being open about this builds trust and helps people make informed decisions.
7. Responsible Use: We need to be careful not to misuse these predictive models. They should be used for the right reasons and not cause harm or panic.
In summary, while predictive analytics can be super helpful in cybersecurity, we also have to deal with challenges like data, evolving threats, and getting results right. Ethically, we have to respect privacy, be fair, and transparent, and use these tools responsibly. It’s a balance between making our digital world safer and respecting individual rights and values.
Future Directions and Innovations
Let’s talk about where AI-driven cybersecurity is headed in the future.
Future Directions and Innovations in AI-Driven Cybersecurity
The world of cybersecurity is evolving, and AI is playing a big role. Here’s where we’re headed:
1. AI and Threat Intelligence: AI is teaming up with threat intelligence. This means AI systems are always checking for new threats. They collect lots of data and analyze it in real time. This helps organizations find out about cyber threats as soon as they pop up.
2. Deception Tech with AI: We’re also seeing more AI in deception technology. These systems trick hackers by making fake stuff in a network. This confuses the attackers and helps security teams find and stop threats faster. AI makes these tricks even better by learning from how hackers work and making the fake stuff seem real.
3. AI-Powered Security Analytics: AI is helping us look at data better. It checks network traffic, user behavior, and system logs. If something looks weird, it raises a flag. This way, we can stop problems before they get big.
4. Automation and Orchestration: AI is also making our response to threats faster. Some systems use AI to figure out what to do when a threat is found. They can even do some things automatically, which means we’re faster at stopping threats, and there are fewer mistakes.
5. Autonomous Cybersecurity: This is a big one. We’re working on systems that can handle cybersecurity all on their own. They can make decisions and take action without people getting involved. This could be a game-changer, making our digital world safer 24/7.
In the end, AI is going to change how we do cybersecurity. These new trends and ideas don’t just help us find and stop threats; they also make us better at it. So, the future looks bright for keeping our digital stuff safe.
Cutting-edge research and Developments in AI For Cybersecurity.
Let’s talk about the latest research and advancements in using AI for cybersecurity.
Cutting-edge research and Developments in AI for Cybersecurity
People are pushing the limits when it comes to using AI to make our online world more secure. Here’s what’s happening:
1. Super Smart Algorithms: Researchers are working on super-smart computer programs. These programs can do more than just spot known online threats. They’re learning how to find brand-new ones that we’ve never seen before.
2. Mixing AI with Other Cool Tech: AI isn’t working alone. It’s teaming up with other fancy tech like edge computing, quantum computing, and the Internet of Things (IoT). This mix of technologies helps us deal with all the tricky challenges of our connected online world.
3. AI You Can Understand: AI is getting smarter, but it can sometimes be a bit of a mystery. Researchers are figuring out how to make AI explain itself and show us why it makes the choices it does. This helps us trust AI more and work better with it.
4. Fighting Back Against Tricky Hackers: Bad guys are trying to trick AI. They want to mess with the smart programs we use for security. Researchers are making AI tougher, so it can spot these tricks and keep our digital stuff safe.
So, there’s a lot of exciting stuff happening in AI and cybersecurity. Smart people are working hard to stay ahead of cyber threats and make our digital world safer every day.
The Role of Explainable AI (XAI)
Let’s talk about the important role of Explainable AI (XAI) in cybersecurity.
The Role of Explainable AI (XAI) in Cybersecurity
In the world of cybersecurity, Explainable AI, or XAI, plays a critical role. Here’s why it matters:
1. Transparency: XAI helps make AI models more transparent. When AI identifies a potential cyber threat, it can explain why it made that decision. This transparency is crucial because it helps human cybersecurity experts understand and trust AI’s judgment.
2. Trust and Fine-Tuning: When cybersecurity professionals know why AI flagged something as a threat, they can trust the AI system more. They can also make improvements to the AI model based on its explanations. This fine-tuning enhances the accuracy of threat detection.
3. Compliance and Accountability: In industries like healthcare and finance, there are strict rules about data protection. XAI helps organizations show that their AI-driven cybersecurity systems work transparently and ethically. This transparency is crucial for compliance and accountability.
In summary, Explainable AI (XAI) in cybersecurity ensures that AI systems are transparent and understandable. This transparency helps cybersecurity experts investigate threats effectively, reduce false alarms, and meet regulatory requirements. It bridges the gap between AI’s power and human understanding, making AI-driven cybersecurity systems more effective and reliable.
Now, let’s discuss the proposal of frameworks for transparent and interpretable AI-driven threat detection.
Proposing Frameworks for Transparent and Interpretable AI-Driven Threat Detection
We’re suggesting something important: creating frameworks that make AI-driven threat detection transparent and understandable. Here’s why this is a big deal:
1. Transparency Matters: We want AI systems to be clear about how they make decisions. When AI identifies a threat, it should explain why it thinks something is dangerous. This way, cybersecurity experts can check if AI is right and act accordingly.
2. Going Beyond Transparency: We’re not stopping at transparency. We also want AI to give us meaningful insights. This means AI should not only show its decisions but also explain which factors influenced those decisions. This helps cybersecurity experts make informed choices based on AI’s threat assessments.
3. Collaboration is Key: Our goal is to create teamwork between AI and human experts. We believe that AI and humans both have strengths. AI is good at spotting threats fast, and humans are great at understanding complex situations. So, we want to combine the best of both worlds.
In short, proposing these frameworks is a big step toward building cybersecurity solutions that work well and make sense. We’re not just looking for effective threat detection; we’re aiming for understanding, trust, and accountability. It’s all about using AI responsibly and ethically to keep our digital world safe and secure.
Conclusion
AI in cybersecurity started as a helpful tool and has now become a central part of our fight against threats. It keeps adapting to new attack methods. This helps cybersecurity experts better detect and respond to threats also AI systems can quickly analyze lots of data, find anomalies, and even take automated actions to make cybersecurity efforts more efficient. We should invest in research to keep up with new cyber threats, improve AI models, encourage collaboration between AI and cybersecurity experts, address ethical and privacy concerns, follow continuous monitoring, integrate threat intelligence, and regularly update AI models.