Zero Trust Protocol And Homomorphic Encryption: Fortify Your Privacy Vault
Trust is like the glue that holds businesses together, relying on relationships and shared understanding. But when it comes to keeping things secure, trust becomes a shaky foundation, especially with the increasing digital threats. Enter Zero Trust Protocol, challenging the assumption of trust in cybersecurity’s complex realm.
Zero trust protocol high level lookup
Zero Trust Protocol is a security framework that challenges the traditional notion of trust based on network location. It requires continuous verification for every user and device, regardless of their location, to minimize the risk of unauthorized access and data breaches. The approach assumes that threats can come from both inside and outside the network, prioritizing authentication and authorization for every access attempt.
Let’s understand it with analogy
Imagine the Zero Trust protocol as a sophisticated art gallery security system. Traditionally, gallery security might rely on securing the entrance and assuming that anyone inside is trustworthy. However, with Zero Trust, the gallery employs a vigilant curator who treats every visitor as a potential art thief until proven otherwise.
In this analogy, each visitor must go through a meticulous authentication process.”Visitors must provide multiple forms of ID and answer art-related questions for access. Clearance determines section entry.”
The gallery is divided into various rooms, each housing unique and valuable artworks. Access to these rooms is strictly controlled, and visitors are only allowed into spaces relevant to their interests (micro-segmentation). Surveillance cameras and motion detectors constantly monitor the gallery, with any suspicious behavior triggering alarms (continuous monitoring).
“To enhance security, we enclose each artwork in a protective casing that requires a special code for unlocking (encryption).” The curator regularly changes these codes to prevent unauthorized access. “We carefully track and analyze every visitor’s movement and interaction with the artworks (authentication and authorization).”
The curator evaluates the trustworthiness of each visitor based on their behavior, knowledge of art, and past visits to the gallery (device trustworthiness). If a visitor starts acting unusually or attempting to access restricted areas, the curator intervenes immediately. The security measures are not static; they adapt to the evolving gallery environment and potential risks (adaptive security).
“In summary, the Zero Trust protocol challenges location-based trust, prioritizing continuous verification and limited access for heightened security.”
Zero trust Protocol Architecture
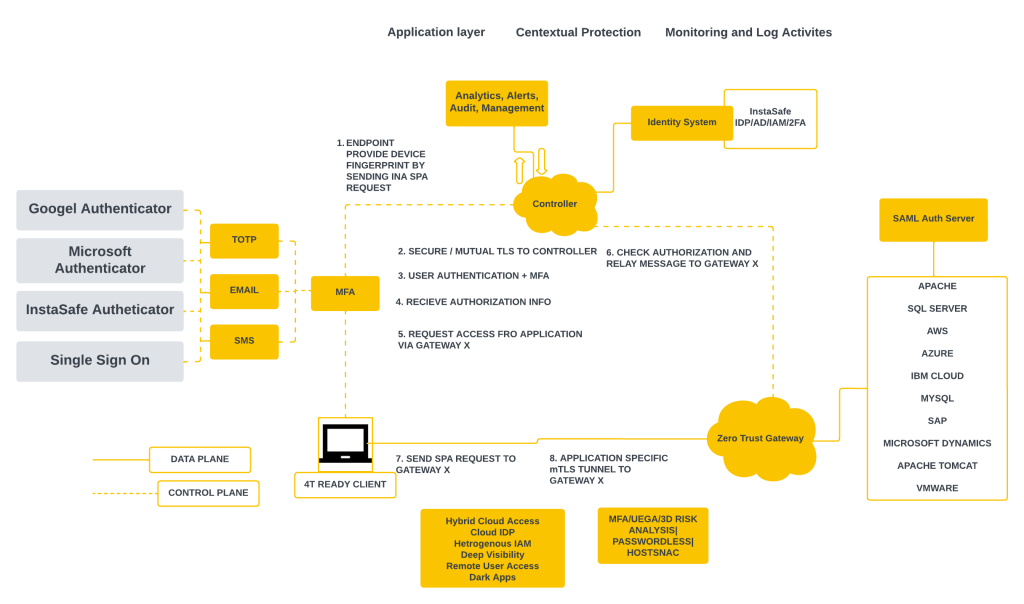
More on Zero trust Protocol
1. User and Device Authentication:
Zero Trust places a strong emphasis on robust authentication mechanisms, including multi-factor authentication (MFA). The verification process extends beyond user credentials, considering the health and trustworthiness of the accessing device.
2. Continuous Monitoring and Behavioral Analysis:
Continuous monitoring and behavioral analysis are integral to the Zero Trust framework. Real-time tracking enables the detection of anomalies, triggering immediate responses to potential security threats.
3. Endpoint Security:
Securing endpoints, such as laptops and smartphones, is pivotal in the Zero Trust model. Robust endpoint security solutions prevent unauthorized access and fortify defenses against potential breaches.
4. Risk-Based Decision-Making:
Zero Trust incorporates risk-based decision-making, dynamically adjusting access decisions based on the risk profile of users, devices, and contextual factors.
5. Integration with Security Policies:
Aligning Zero Trust principles with comprehensive security policies is crucial. Zero Trust is not just a technological solution but a holistic security strategy involving policy enforcement and regular assessments.
Homomorphic Encryption
Homomorphic encryption is a privacy-preserving cryptographic technique that allows computations to be performed on encrypted data without decrypting it first. In simpler terms, it enables operations on data while it remains in an encrypted state, providing a way to maintain privacy during computations.

Think of homomorphic encryption like the way a sniffer dog at the airport works to keep your privacy intact. The dog can sniff out potentially harmful stuff in your bags without checking out what’s inside. Homomorphic encryption does a similar trick but with your data. It lets you analyze encrypted data without exposing the actual details to the systems or people doing the analysis.
So, just as the airport dog doesn’t actually see what’s in your bag, homomorphic encryption lets operations happen on your encrypted data (like a secret code) without anyone needing to know the real, sensitive info. It’s like doing secret math on your data to get useful results without revealing what the data actually is.
Analogy
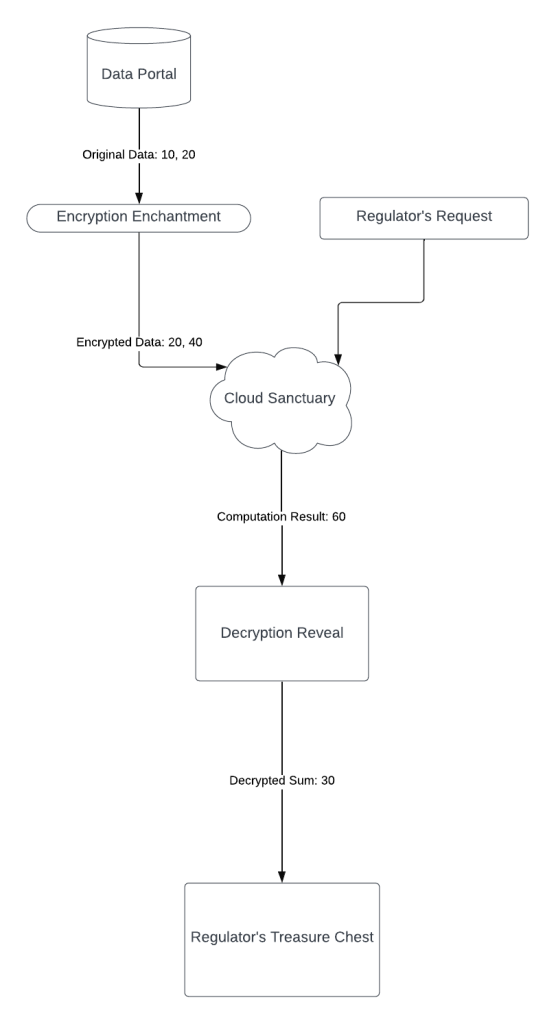
In this scenario, the bank employs homomorphic encryption to secure its confidential data set, comprising the numbers 10 and 20. Using a homomorphic encryption scheme, the bank multiplies each element in the set by 2, resulting in an encrypted data set of 20 and 40. The bank then entrusts this encrypted set to a cloud provider for storage and analytics. When a financial regulator requests the sum of the secret data elements, the bank instructs the cloud provider to perform the operation.
Remarkably, the cloud provider, working solely with the encrypted data set, computes the sum of 20 and 40 without accessing the actual values, yielding a result of 60. Importantly, the cloud provider never gains visibility into the original secret data due to the homomorphic encryption employed. The bank subsequently decrypts the result, revealing the sum of the original data set as 30, which is then provided to the financial regulator. This showcases the practical utility of homomorphic encryption in enabling secure and privacy-preserving computations on sensitive data.
This is one of the example where we can use these types of cybersecurity algorithms
Another Analogy
Alice, concerned about the privacy of her health data, opted to utilize homomorphic encryption when seeking insights from XYZ Hospital’s trained health detection model. Rather than directly sharing her detailed health report, Alice encrypted the information using the hospital’s public key. This encrypted health report was transmitted to the hospital, where their health detection model performed computations on the encrypted data without the need for decryption.
The hospital then sent the encrypted health analysis result back to Alice, who, possessing the corresponding private key, could decrypt the information and gain insights into her health status. This innovative use of homomorphic encryption ensured that sensitive health data remained confidential throughout the process, allowing Alice to access valuable health assessments while preserving the privacy of her personal information.
Varieties of Homomorphic encryption
Partially Homomorphic Encryption (PHE):
Allows for the evaluation of only one type of mathematical operation on encrypted data. PHE can be either additive or multiplicative, meaning it supports addition or multiplication operations while keeping the data encrypted.
Somewhat Homomorphic Encryption (SHE):
Extends the capabilities of PHE by supporting both addition and multiplication operations on encrypted data. However, it has limitations on the number of sequential operations that can be performed before decryption is required.
Fully Homomorphic Encryption (FHE):
Offers the highest level of homomorphic capabilities by supporting an unlimited number of both addition and multiplication operations on encrypted data. FHE allows for complex computations while the data remains in an encrypted state, enabling a broader range of privacy-preserving applications.
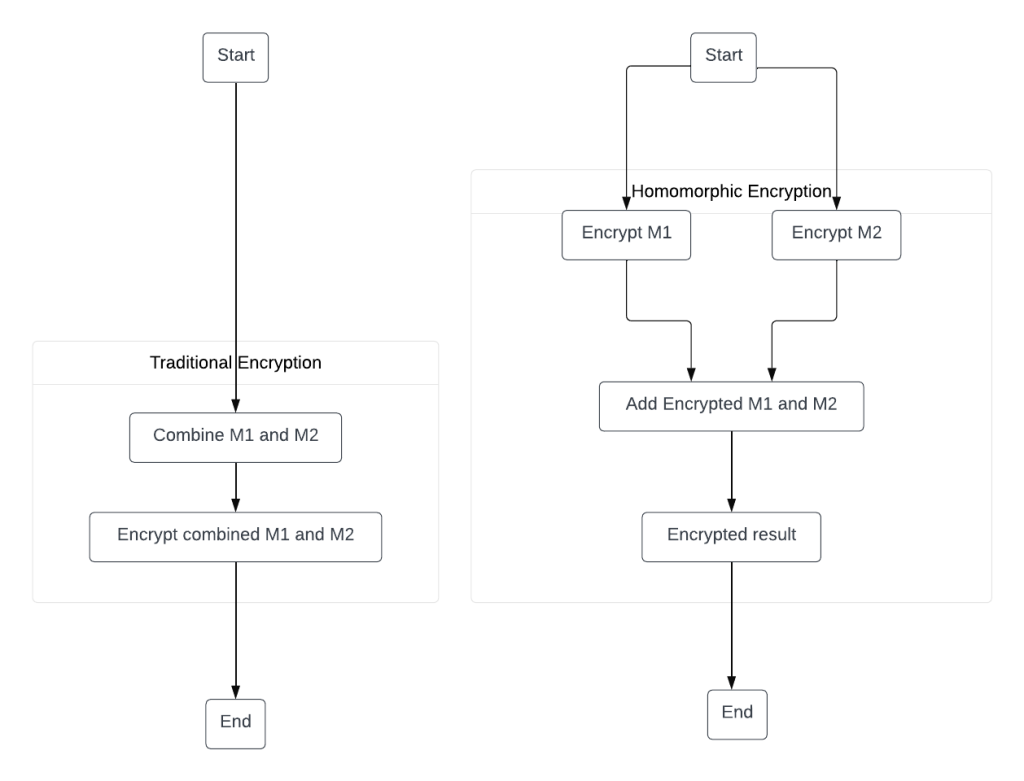
Combination
Zero Trust ensures that access is verified and authenticated at every step:
In a traditional security model, there is often a default trust within a network. Once a user gains access, they may navigate freely within the network with the assumption of trust. Zero Trust challenges this by requiring verification and authentication for every access attempt, regardless of the user’s location or previous access history. Each interaction is treated as potentially untrusted, and individuals or devices must authenticate themselves before gaining access, even if they are already inside the network.
Homomorphic encryption enables secure computation on encrypted data:
Homomorphic encryption is a cryptographic technique that allows computations to be performed on encrypted data without the need to decrypt it. In simpler terms, data is encrypted, and mathematical operations can be conducted on the encrypted data itself. The results of these operations, when decrypted, are equivalent to what would have been obtained if the operations were performed on the unencrypted data. This allows for secure processing and analysis of sensitive information without exposing the actual data to those performing the computations.
Combining these concepts, Zero Trust ensures that each access attempt is rigorously authenticated, and homomorphic encryption provides a layer of security by allowing computations on encrypted data. This way, even if a user or system gains access, the actual data remains confidential, and any processing or analytics can be performed securely on the encrypted information. The synergy of Zero Trust and homomorphic encryption strengthens overall data security and privacy measures in an organization.
Conclusion
In a nutshell, when Zero Trust Protocol teams up with homomorphic encryption, it’s like putting on a superhero cape for cybersecurity. It not only tackles today’s online security challenges but also sets the stage for a future where keeping our digital stuff safe is tougher and easier at the same time. Picture it as a robust shield against all those sneaky cyber threats. As these techie tools get even better, we’re heading towards a world where companies can use fancy tech without risking their private data. The future? Well, it looks like a cool mix of strong security, easy access, and keeping our digital secrets super safe.
Check out my previous blogs: NFT-ARTChain